
Maintaining the crucial specialized cyber security knowledge necessary, especially OT (Operational Technology) by yourselves is cost- and ressource-intensive. We provide you with the know-how on a flexible basis at any time. In this way, you have comprehensive dynamic support for your information security at all times. Our cyber security services prepare your critical infrastructure to the required level, increasing resilience for new threats at any time.
CISO_as_a_Service_2024.pdf [Only available in German]
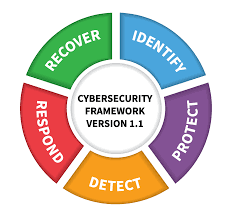



Whitepaper only available in German.
Gerade in industriellen Umgebungen von kritischen Infrastrukturen ist ein Betrieb mit hoher Verfügbarkeit, möglichst ohne jede Unterbrechung der Produktionsprozesse, absolut unabdingbar. Das Thema Business Continuity Management (BCM) spielt im Kontext der Security in diesem Bereich eine besonders grosse Rolle. Wenn ein Cyberangriff erfolgt und dadurch Infrastruktur lahmgelegt wird, müssen möglichst typengleiche Systeme (Hardware) als Ersatzsysteme mit kompatibler Software (Firmware, Betriebssystem) unmittelbar bereitstehen, damit Backups zurückgespielt und Systeme wiederhergestellt werden können. Bis dies erfolgt ist, müssen zudem Ersatzprozesse möglichst sofort in Kraft treten.